ChatBunker preserves user functionality while remaining HIPAA compliant.
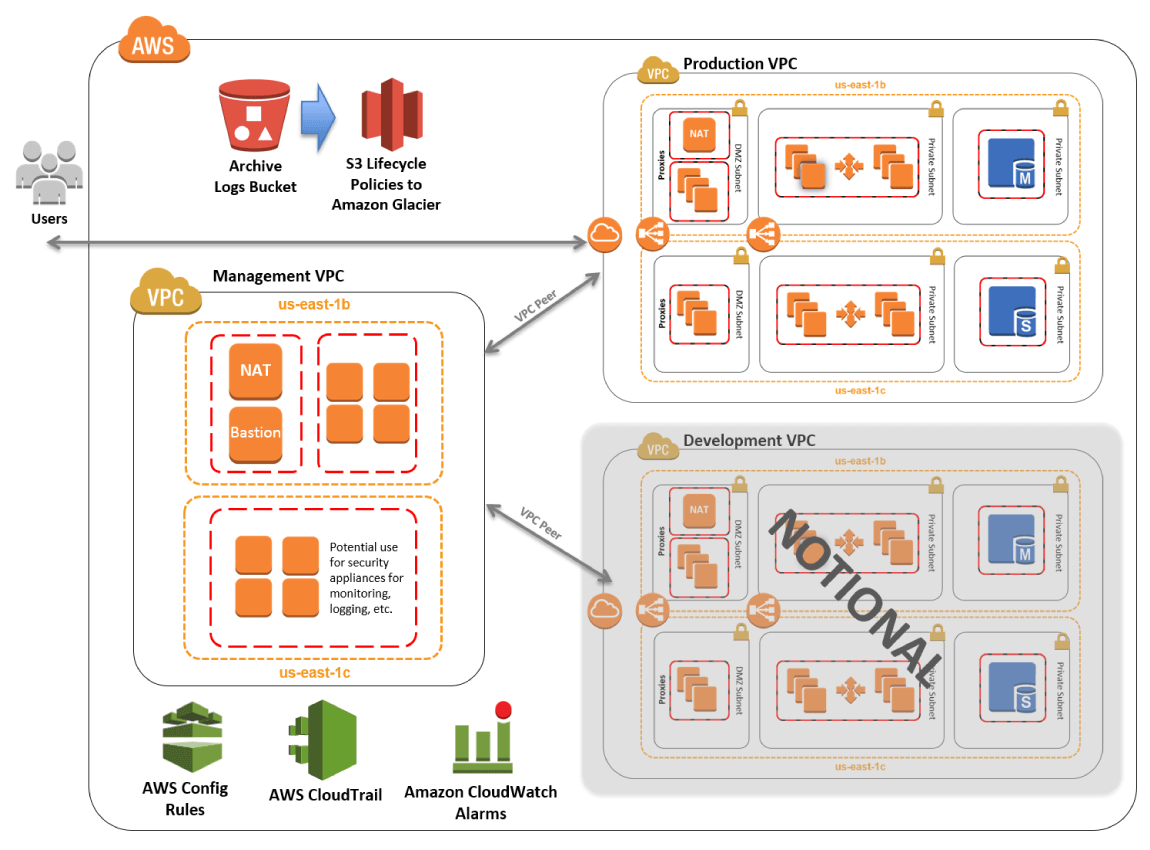
ChatBunker’s architecture is based on the “HIPAA on AWS Enterprise Accelerator” architecture, recommended by industry-leading Amazon Web Services, a secure cloud service platform. It has been specifically designed to support a HIPAA compliant program.
Our infrastructure is supported by the industry-leading Amazon Web Services (AWS). AWS is a secure cloud services platform, offering compute power, database storage, content delivery and other functionality to help businesses scale and grow.
ChatBunker’s architecture is based on the “HIPAA on AWS Enterprise Accelerator” architecture recommended by AWS. It has been specifically designed to support a HIPAA compliance program
The focus of ChatBunker’s security program is to prevent unauthorized access to customer data. To this end, we take exhaustive steps to identify and mitigate risks, implement best practices, and constantly evaluate ways to improve.

ChatBunker transmits data over public and private networks using strong encryption that supports the latest recommended secure cipher suites to encrypt all traffic in transit, including use of TLS 1.2 protocols, AES256 encryption, and SHA2 signatures, as supported by the clients. ChatBunker monitors the changing cryptographic landscape and upgrades the cipher suite choices as the landscape changes, while also balancing the need for compatibility with older clients.
Data at rest in ChatBunker’s production network use two leading technologies from AWS:
Amazon RDS encrypted instances using the industry standard AES-256 encryption algorithm. All database snapshots are encrypted as well.
EBS encrypted volumes using the industry-standard AES-256 algorithm for encryption keys. Encryption operations occur on the servers that host EC2 instances, ensuring the security of both data-at-rest and data-in-transit between an instance and its attached EBS storage.
AWS data centers offer state-of-the-art physical protection for the servers and related infrastructure that comprise the operating environment for the ChatBunker service. AWS is responsible for restricting physical access to ChatBunker’s systems to authorized personnel.

ChatBunker divides its systems into separate networks to better protect more sensitive data. Systems supporting testing and development activities are hosted in a separate network from systems supporting ChatBunker’s production website. Customer data submitted into the ChatBunker services is only permitted to exist in ChatBunker’s production network, its most tightly controlled network.
Administrative access to systems within the production network is limited to those engineers with a specific business need.
Network access to ChatBunker’s production environment from open, public networks (the internet) is restricted. Only a small number of production servers are accessible from the internet. Only those network protocols essential for delivery of ChatBunker’s service to its users are open at ChatBunker’s perimeter. Changes to ChatBunker’s production network configuration are restricted to authorized personnel.

In sophisticated enterprise AWS deployments like ChatBunker’s, Amazon’s Identity Access Management (IAM) service controls access, enforces protections, and provides granular control over hundreds or even thousands of account users. IAM policies are the bedrock of security in any AWS environment.
In our HIPAA-compliant chat platform, we believe the use of IAM security is essential. HIPAA requires central identity management and necessitates the close control of access to data. IAM policies are key in managing control to ChatBunker’s resources and data they hold.
Where possible and appropriate, ChatBunker uses private keys for authentication. Where passwords are used, the passwords themselves are required to be complex (longer than 12 characters, and not consisting of a single dictionary word, among other requirements).
ChatBunker uses a password manager. Password managers generate, store and enter unique and complex passwords. Use of a password manager helps avoid password reuse, phishing, and other behaviors that can reduce security.

ChatBunker uses CloudWatch to monitor servers and retain and analyze a comprehensive view of the security state of its corporate and production infrastructure.
Chabunker uses AWS CloudTrail to enable governance, compliance, and operational and risk auditing. Actions taken by a user, role, or an AWS service are recorded as events in CloudTrail. Events include actions taken in the AWS Management Console, AWS Command Line Interface, and AWS SDKs and APIs.
Visibility into such account activity is a key aspect of security and operational best practices. ChatBunker uses CloudTrail to view, search, download, archive, analyze, and respond to account activity across its AWS infrastructure. We can identify who or what took which action, what resources were acted upon, when the event occurred, and other details to help us analyze and respond to activity in our AWS account.

ChatBunker uses Amazon GuardDuty, a continuous security monitoring service that analyzes and processes VPC Flow Logs, AWS CloudTrail event logs, and DNS logs. It uses threat intelligence feeds, such as lists of malicious IPs and domains, and machine learning to identify unexpected and potentially unauthorized and malicious activity within ChatBunker’s environment.
This can include issues like escalations of privileges, uses of exposed credentials, or communication with malicious IPs, URLs, or domains. It also monitors AWS account access behavior for signs of compromise, such as unauthorized infrastructure deployments, like instances deployed in a region that has never been used, or unusual API calls, like a password policy change to reduce password strength.

ChatBunker has implemented appropriate safeguards to protect the creation, storage, retrieval, and destruction of secrets such as encryption keys and service account credentials.
We take security seriously at
ChatBunker,
because every person and team using our service expects their data to be secure and confidential.
Safeguarding this data is a critical responsibility we have to our customers, and we work hard to maintain that trust.